Backdoor. exploit. file. internet. software Line Icon in Mobile for Download Page 13029655 Vector Art at Vecteezy

EXPLOIT Printed Stylish Back Cover for Realme 9i, Oppo A76, Oppo K10, Oppo A96/ Sports 627 : Amazon.in: Electronics

GitHub - blue0x1/mobilemouse-exploit: Mobile Mouse 3.6.0.4 could allow a remote attacker to execute arbitrary code on the system, caused by improper input validation. By sending a specially-crafted request, an attacker could exploit

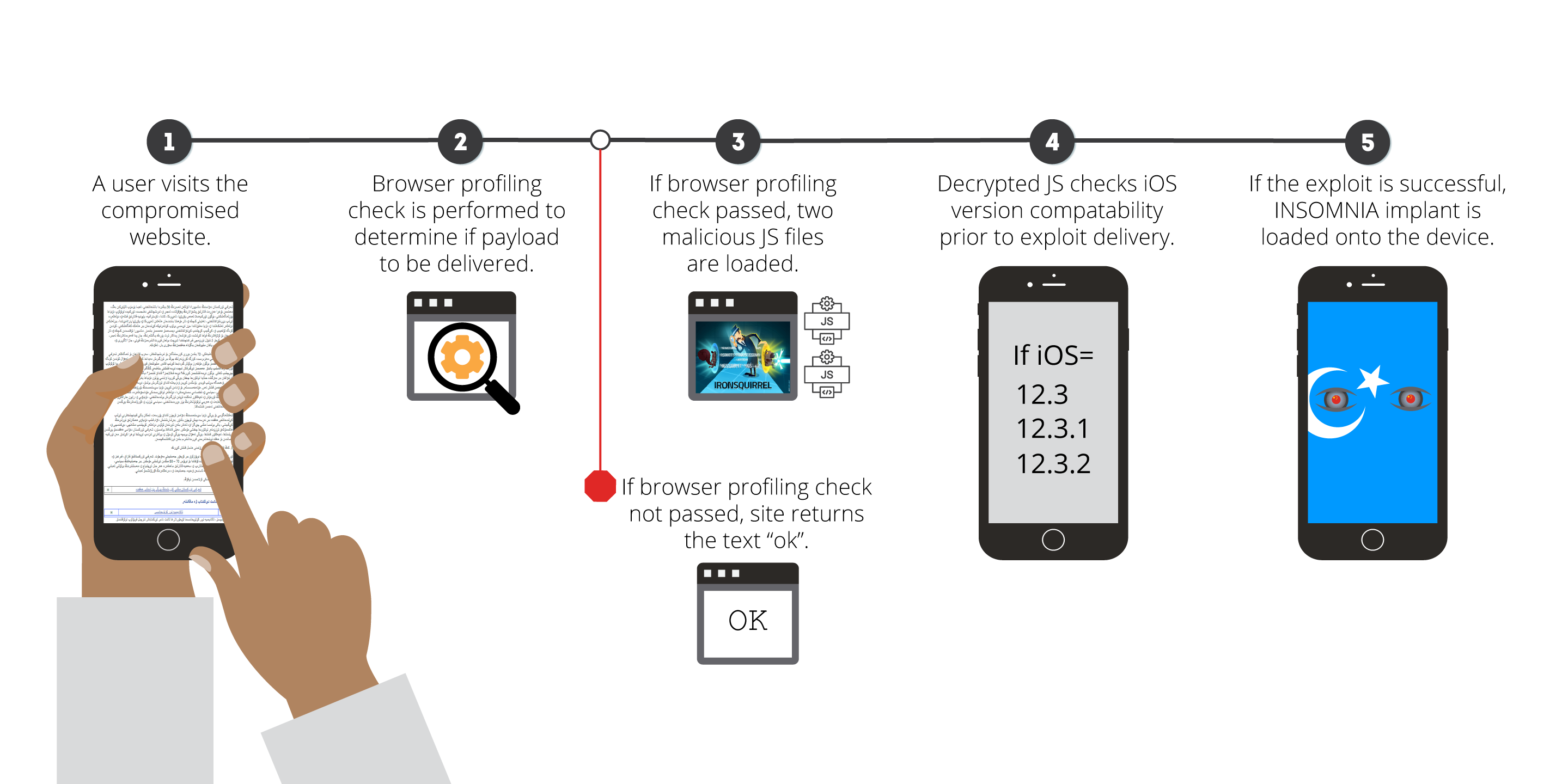
Spyware vendors use exploit chains to take advantage of patch delays in mobile ecosystem | CSO Online