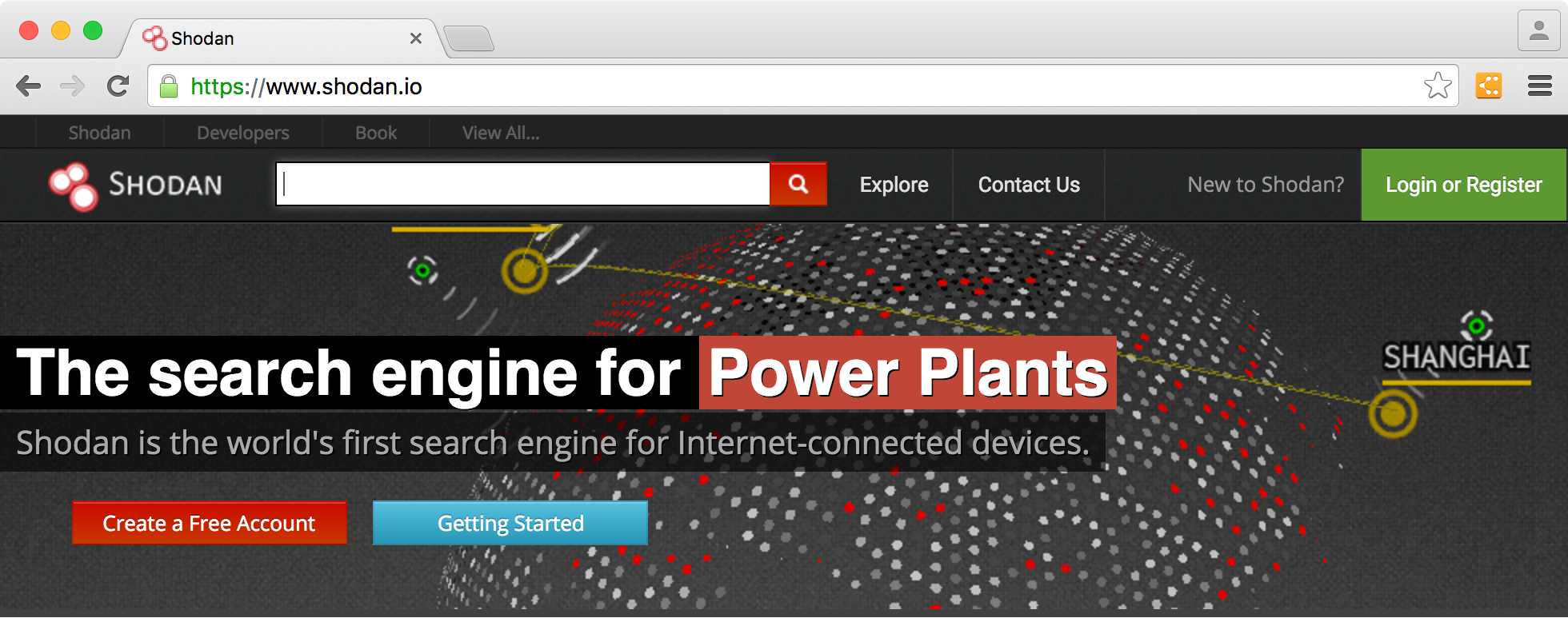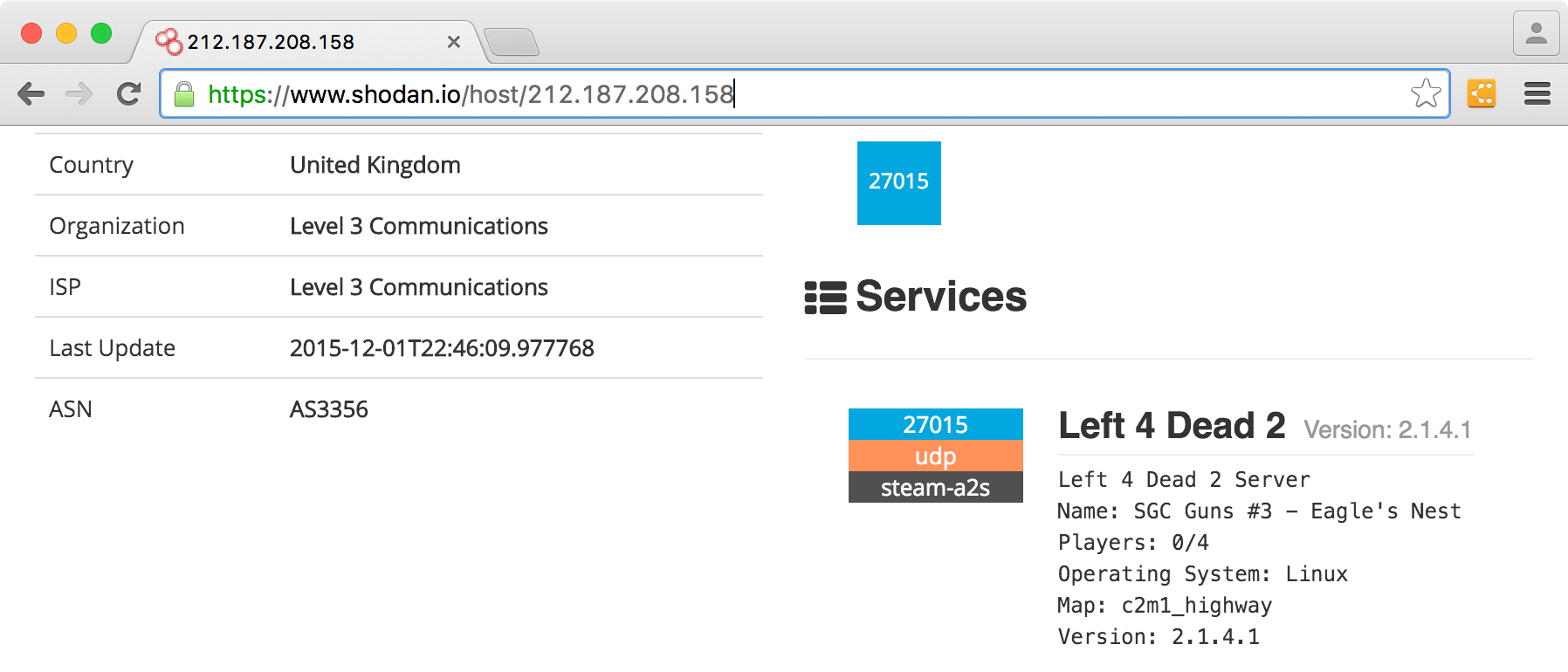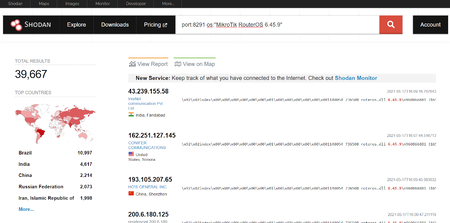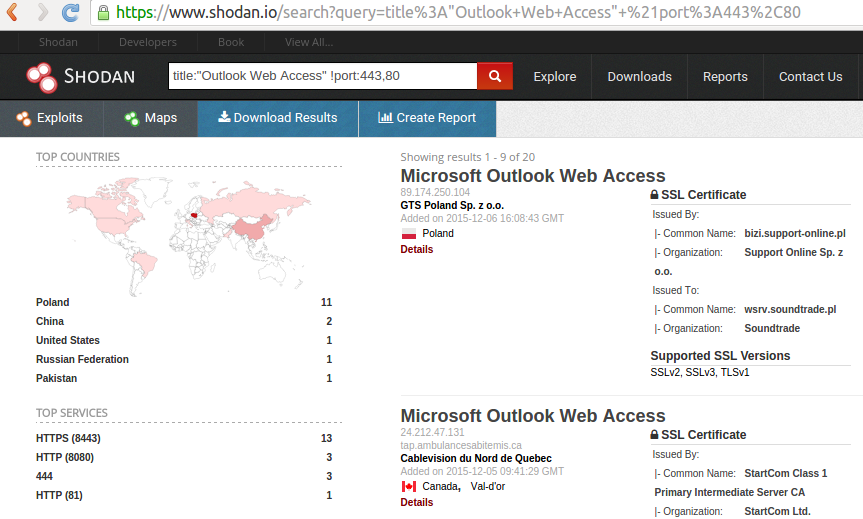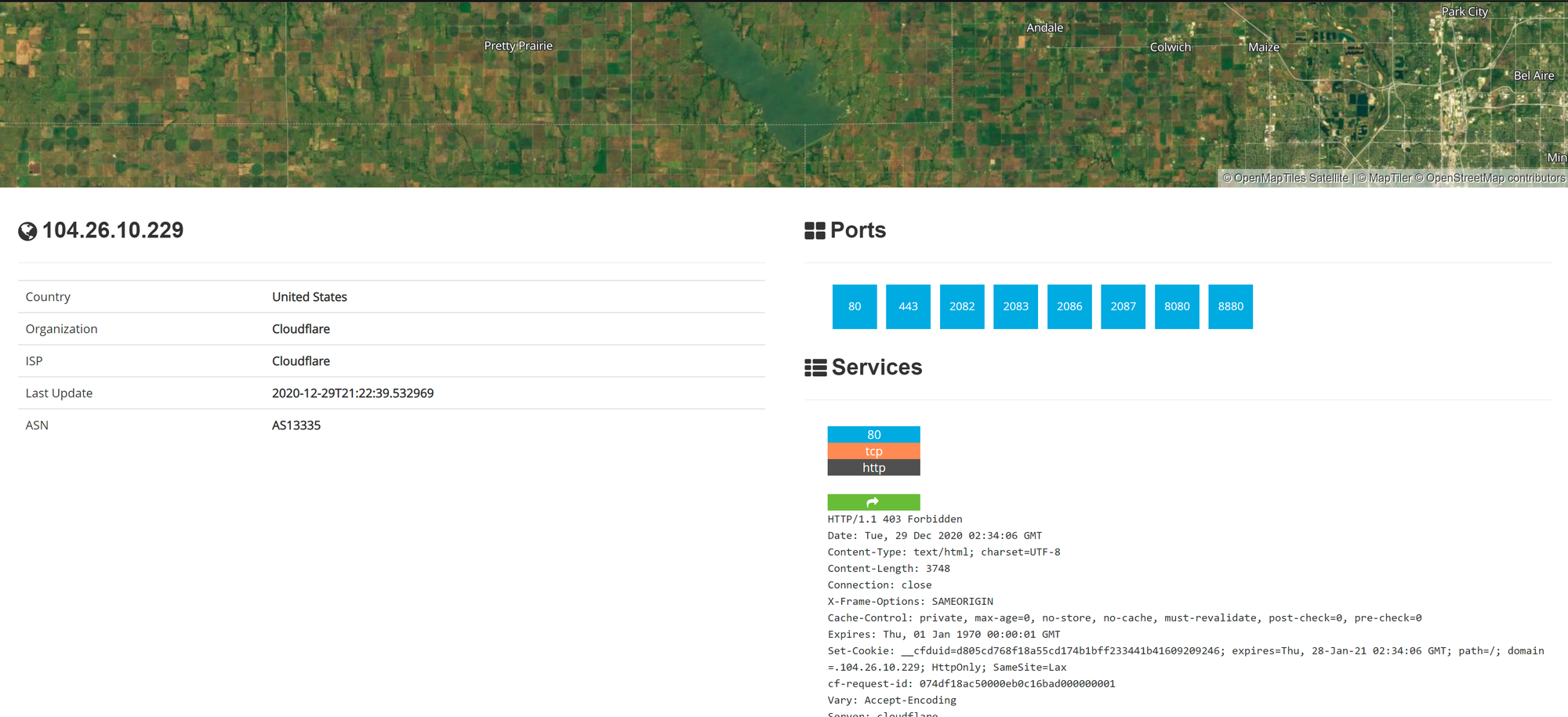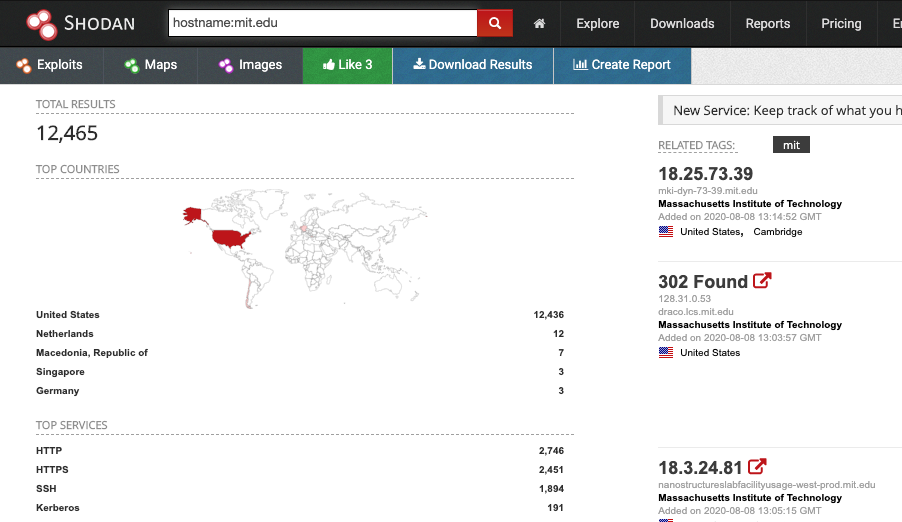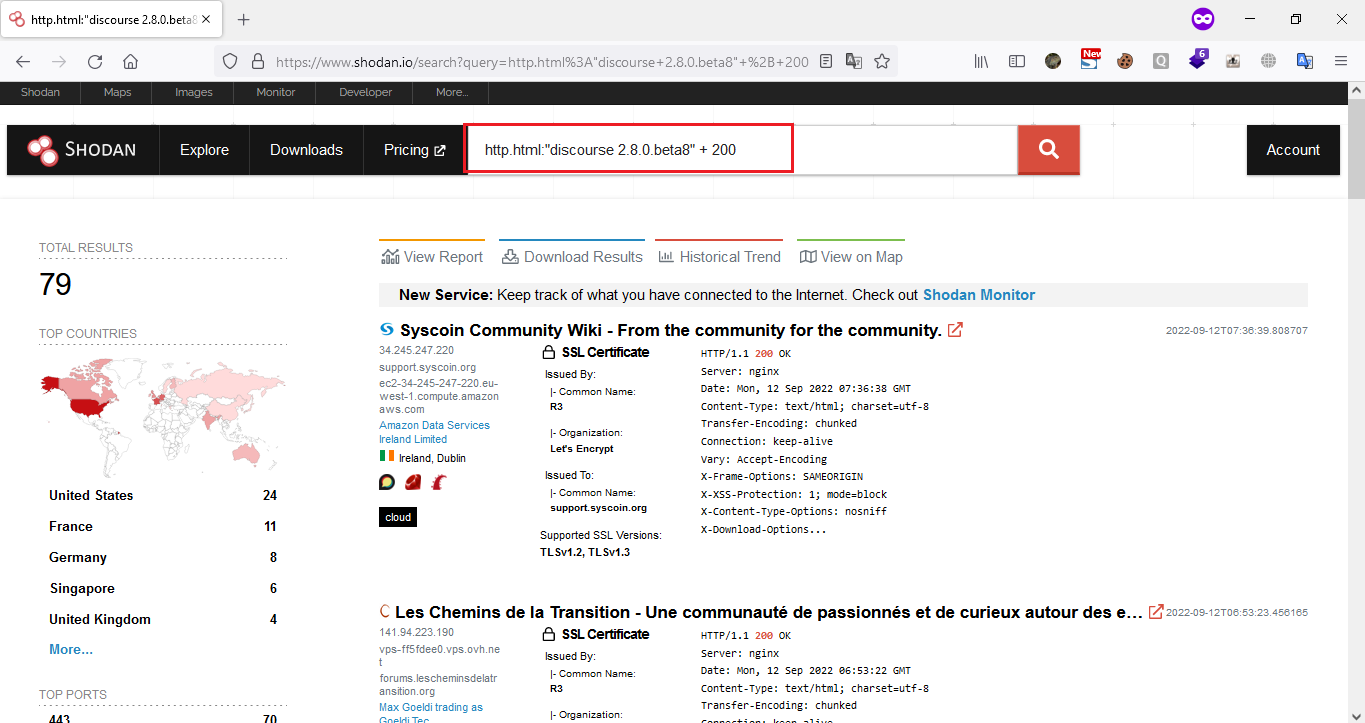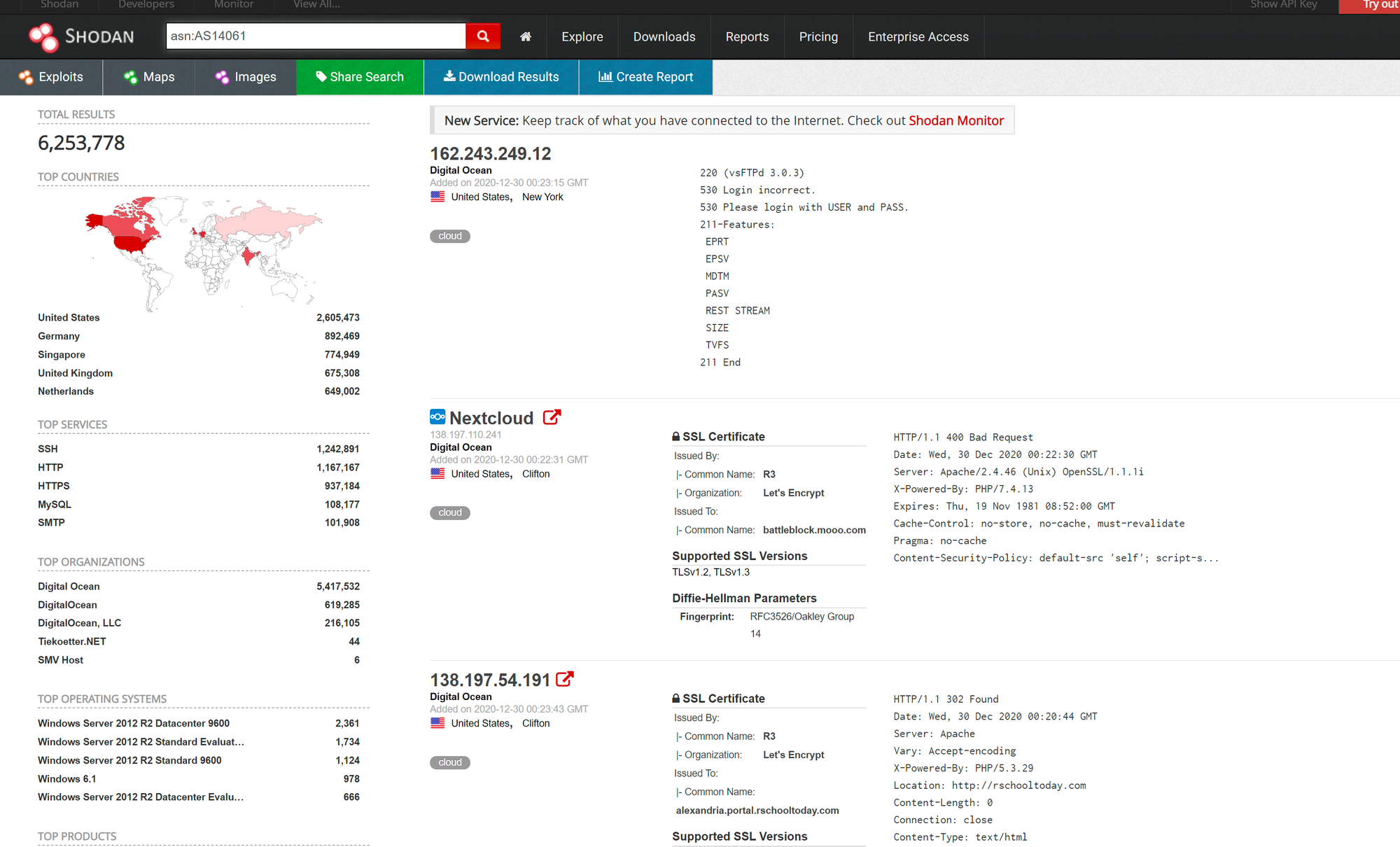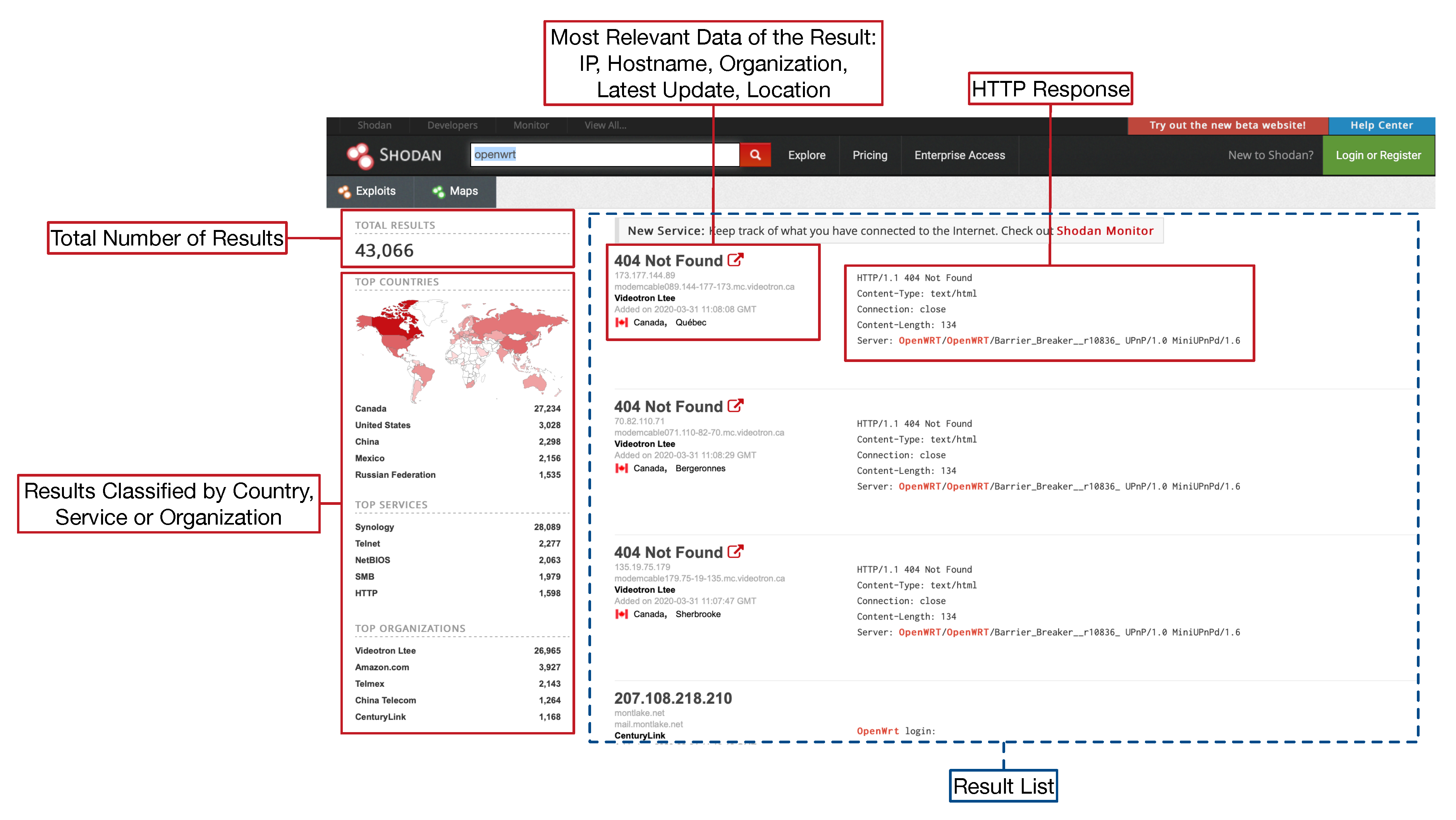
Sensors | Free Full-Text | Teaching and Learning IoT Cybersecurity and Vulnerability Assessment with Shodan through Practical Use Cases
![Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : root@HackingPassion.com-[~] Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/wp-content/uploads/2020/03/shodan-api-key.png)
Shodan Command Line a Step by Step Walkthrough - HackingPassion.com : [email protected][~]
GitHub - S-RM/HistoricShodanScanner: A simple utility to quickly gather historic Port and CVE exposures from an IP range.